You are here: Foswiki>KnowledgeBase Web>PfsenseBasicSetup (05 Aug 2022, NickDemou)Edit Attach
pfSense Basic Setup
- pfSense Basic Setup
- If you load the BasicSetup:
- First Steps
- System > General Setup
- System > Advanced > Admin Access
- Interfaces > WAN
- Firewall > Rules > Wan
- Status > System Logs > Settings
- If you need a Dynamic DNS address for your WAN(s)
- If you're connecting a typical ADSL modem router
- ntopng
- Status > Monitoring
- If you have multiple WANs
- Optional
- If you want a wifi interface
If you load the BasicSetup:
change :- admin password
- hostname
- domain
- dns servers
First Steps
Text console > 1 Assign Interfaces Text console > 2 Set Interfaces IP address Follow the WebUI WizardSystem > General Setup
Never forget to complete settings there carefully.System > Advanced > Admin Access
Protcol: [x] HTTPS TCP Port: 61234 Secure Shell Server: [x] Enable Secure Shell SSH port: 61235 Check [v] Disable HTTP Refere enforcement(alternatively for more security you can leave it unchecked but add all possible hostnames --e.g. static IPs or dynamic dns host names-- you will use to access the WebUI)
Interfaces > WAN
If the WAN IP is 192.... or 10.... or 172.1... goto WAN configuration and uncheck[ ] Block Bogon Networks
Firewall > Rules > Wan
Add rule: Protocol TCP, Destination Port Range 61234 - 61235, Description: Allow WebUI and SSH from WAN [do the same for other WAN interfaces if any] [todo] Please read this: https://doc.pfsense.org/index.php/How_can_I_access_the_webGUI_from_the_WANStatus > System Logs > Settings
If you have ~200MBytes free on your disk set Log file size (Bytes) to 10100100 (about 10MBytes per log file) to keep logs for more time.If you need a Dynamic DNS address for your WAN(s)
Part 1 - creating Dynamic DNS entries
Goto Services > Dynamic DNS > Dynamic DNS Clients and create an entry with the Dynamic DNS you wish Repeat for all WAN Interfaces with dynamic DNSPart 2 - hack to keep DNS records updated at most every 5min
Goto System > Package Manager > available Packages Search for cron and install it Goto Services > Cron Locate the line about /etc/rc.dyndns.update and click edit Change minute to */5 and hour to *If you're connecting a typical ADSL modem router
Don't forget to configure your modem like this: 1)disable the firewall / DMZ to the WAN ip of pfsense (usually static bind from the router) 2)Port forward all ports to the WAN IP of pfSense ΕΚΤΟΣ ΑΝ ΕΙΝΑΙ COSMOTE ΕΥΡΥΖΩΝΙΚΗ οπότε προωθήστε τις πόρτες 1-1024 & 16000-65535 3)If you already have and Access Point DISABLE the wifi of the modem.ntopng
Install ntopng at System > Package Manager > Available Packages Configure it at Diagnostics > ntopng settings (I usually set Configures only LAN net as local because I'm having private IPs for Internet interfaces) then click " Update GeoIP Data" Add a firewall pass rule for ntopng port (3000) at firewall > rules > WAN (and any more WAN ports like OPT1, etc)Status > Monitoring
add graphs for traffic / quality for WAN and VPN connections Status -> Monitoring Settings WANqlt Left Axis :Quality - WAN-DHCP Right Axis : None Option: 1Day-5minutes Settings-Display Advanced -> Add View named as WANqlt WANtrf Left Axis :Quality - WAN-DHCP Right Axis : None Option: 1Day-5minutes Settings-Display Advanced -> Add View named as you WANtrf Follow the process as many time as the WANsIf you have multiple WANs
At *System > General Setup > DNS Server Settings* there should be at least one unique DNS server per gateway.
Example:

create a group named all_lines, add all WANs to with "tier 1".
create a group named sticky_gw, add all WANs begining from the best one at tier 1, next on at tier 2, etc.
create a group named failover_default, add all WANs in different tiers begining with your fastest/stablest one in tier 1
At System > Routing > Gateways > Default gateway IPv4 Default gateway ipv4 = automatic
At System > Routing > Gateways > for every gateway > Edit > advanced settings > monitor IP : an IP on the internet that responds to pings (usualy the DNS server of the ISP, or google DNS or OpenDNS)
DON'T USE THE SAME IP ON MORE THAN ONE GATEWAY
> Data Payload = 1
> Packet Loss Thresholds: 5 min, 10 max for all WAN's except the fastest/better one where you will set it to Payload =1 Packetloss 20-30
*Firewall > Rules > LAN:* (this will be the failover line in case where every other line is congested)
Use the gateway group "all_lines" for all your Internet traffic
Add a rule above the default rule for web banking sites and the like:
*Firewall > Rules > aliases:* Destination addres = always_use_one_wan, advanced > gateway group = sticky_gw
Create an alias named always_use_one_wan and add all IPs of web banking sites and the likes that don't work from multiple WANs.
Services > DNS Resolver & Forwarder:* *Enable DNS forwarder in place of DNS resolver*
: THe reason is that if a WAN connection has any problem (goes down, is overloaded etc) then using the DNS forwarder will avoid a lot of problems from timed out DNS queries because it does parallel queries on all lines (*but DOESN'T support dnssec). The DNS resorvel supports DNSSEC but does not do parallel queries. Even the webUI of pfsense will be slow in case of a WAN line missbehaving.
For more info see this post: Re: DNS Forwarder Stable and faster than DNS Resolver! « Reply #4 on: June 21, 2016, 05:55:42 am » johnpoz Hero Member, Posts: 13693 Karma: +1238/-215 [...] if [you...] really don't give 2 shits about dnssec.. Use dnsmasq (AKA DNS forwarder) since it will forward to all your dns you have listed and use the fastest response..
Optional
To preserve command history in the shell (CLI):echo "set history = 1000" >> /root/.tcshrcecho "set savehist = 1000" >> /root/.tcshrc
If you want a wifi interface
STEP1 Assign an interface
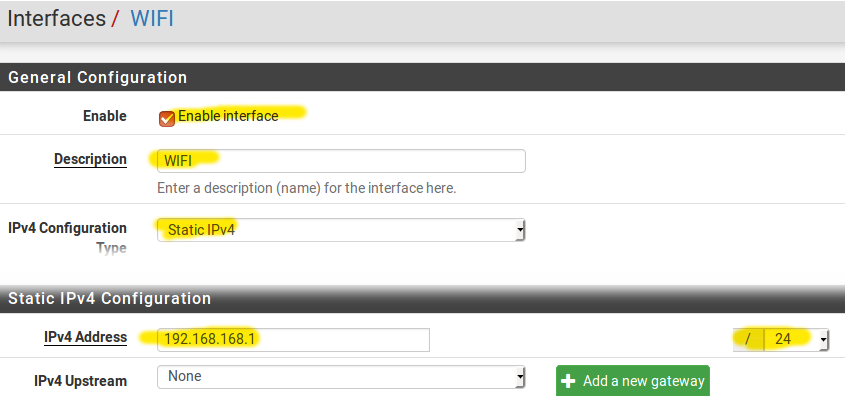
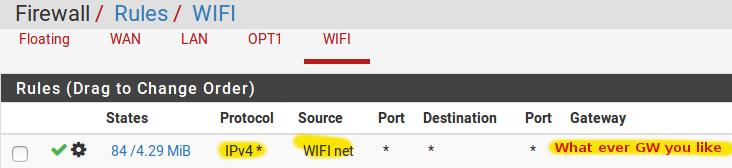
STEP2 Allow access from WIFI to the Internet
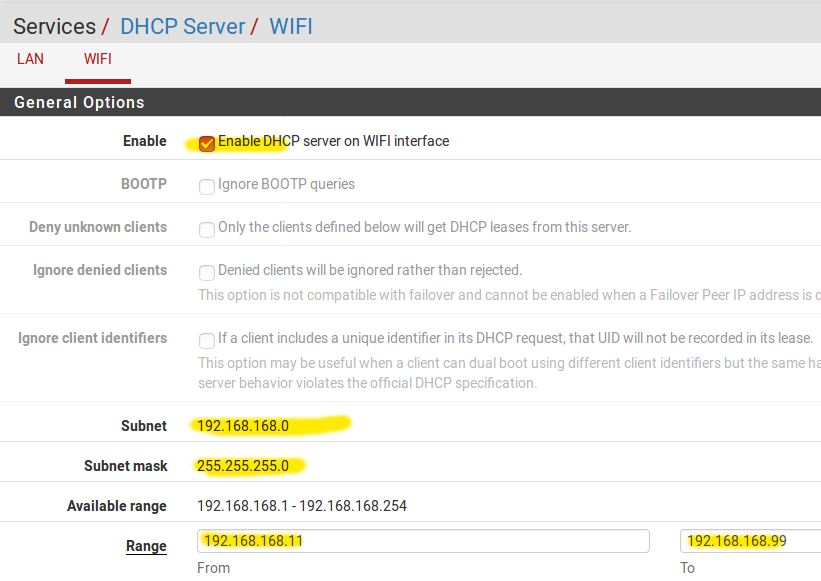
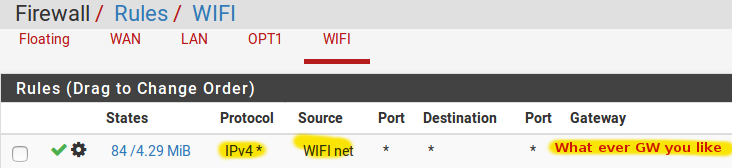
STEP3 Enable DHCP service for the WIFI
- Auto-attached by ImagePlugin:
Edit | Attach | Print version | History: r28 < r27 < r26 < r25 | Backlinks | View wiki text | Edit wiki text | More topic actions
Topic revision: r28 - 05 Aug 2022, NickDemou
- Toolbox
-
 Create New Topic
Create New Topic
-
 Index
Index
-
 Search
Search
-
 Changes
Changes
-
 Notifications
Notifications
-
 RSS Feed
RSS Feed
-
 Statistics
Statistics
-
 Preferences
Preferences
- Webs
-
 KnowledgeBase
KnowledgeBase
Copyright © enLogic
