pfSense Site-2-Site with OpenVPN
Certificates
For the VPN server you'll need a server certificate . You create it at: System > Certificate Manager > Certificates. Click Add First select these two options:Method: [Create an internal Certificate] Certificate Type: [Server Certificate]Then fill all other options like in this example:
Descriptive Name:ath-thes-vpn Country Code: GR State: Attiki City: Athens Organization: Mazars Email Address: admin@mazars.gr Common Name: ath-thes-vpn.mazars.gr
VPN Setup
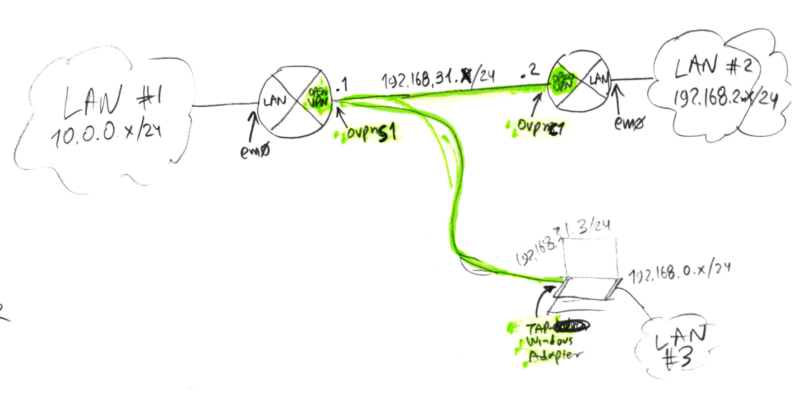
You must note on paper the definition of all 3 networks that are involved: the 2 physical networks that you're gonna connect together AND the virtual network that connects them together. For example- the physical network at the side of the VPN Server is 10.0.0.0/24
- the physical network at the side of the VPN Client is 192.168.2.0/24
- the virtual network that connects them is 192.168.31.0/24
 Then you go to VPN > OpenVPN > Add, select Peer to peer shared key for the VPN type and follow the image bellow. Pink settings must be the same in both sides (server and client). The cyan and green are the network definitions of each side.
Then you go to VPN > OpenVPN > Add, select Peer to peer shared key for the VPN type and follow the image bellow. Pink settings must be the same in both sides (server and client). The cyan and green are the network definitions of each side.
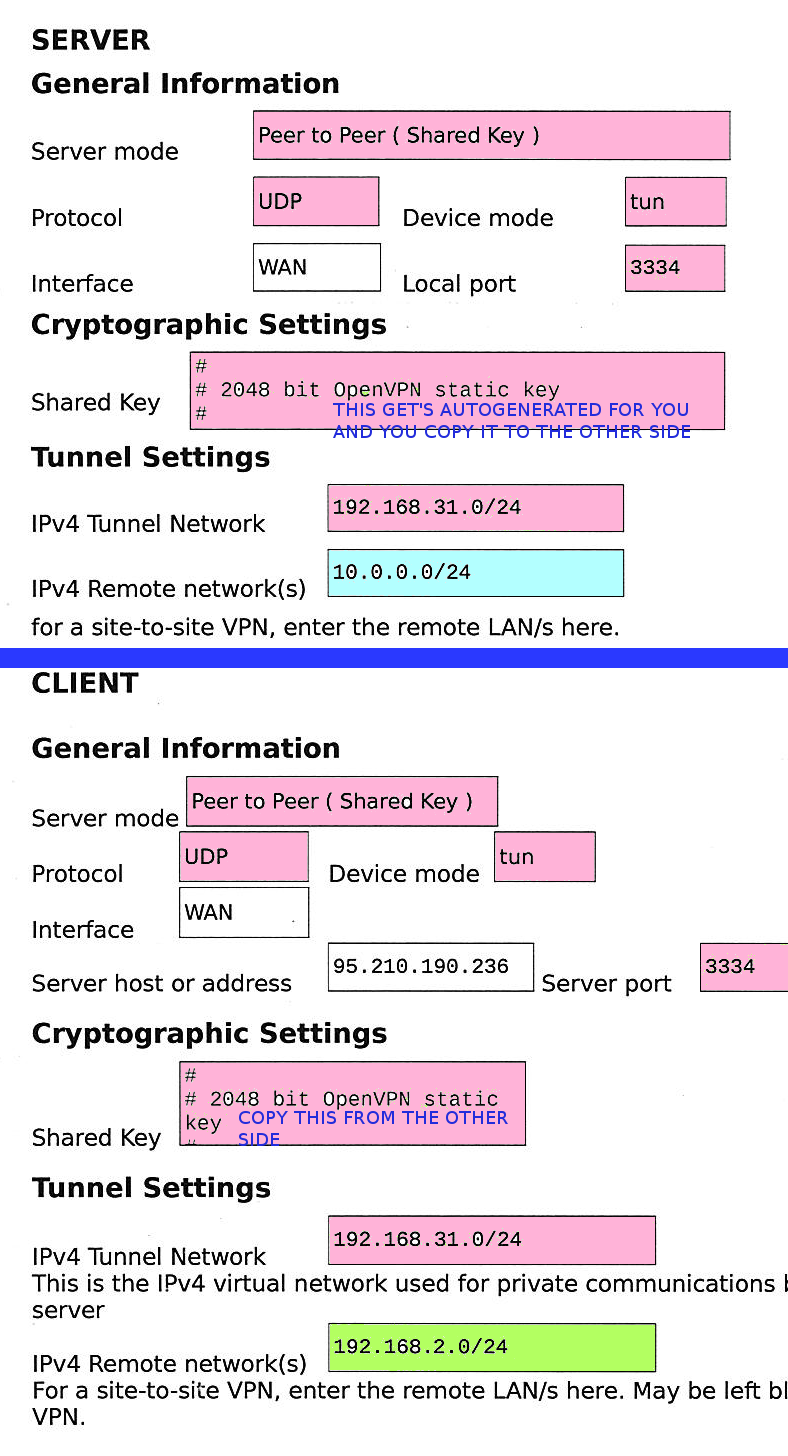 When you create the server leave the option to auto-generate the _Shared Key__. After you save the server settings, open it again, copy the auto-generated _Shared Key. Then proceed to setup the client where you'll clear the option to auto-generate the key and you'll paste the Shared Key you just copied.
If you see this error in the logs: "Authenticate/Decrypt packet error: packet HMAC authentication failed" you're not using the same Shared Key between the two pfsenses.
When you create the server leave the option to auto-generate the _Shared Key__. After you save the server settings, open it again, copy the auto-generated _Shared Key. Then proceed to setup the client where you'll clear the option to auto-generate the key and you'll paste the Shared Key you just copied.
If you see this error in the logs: "Authenticate/Decrypt packet error: packet HMAC authentication failed" you're not using the same Shared Key between the two pfsenses.
After the VPN is up
You must add at least one pass rule to firewall > rules > openvpn (usualy pass for any protocol, any source to any destination)Tests
If the vpn is up but any of the pings bellow fail then check your routing table. Every router must have a route for the remote LAN. If the route doesn't appear, check your VPN settings and in particular the remote network entry. If the routing appears fine check your firewall roules. You can runtcpdump -i ovpnc1/ovpns1/etc to diagnose the issue. If everything is in place check for typos. - Ping from one router the other using their OpenVPN address (virtual network addresses) -- same from the 2nd router
- Ping from one router a host on the other LAN -- same from the 2nd router
- Ping from one LAN host a host on the other LAN-- same from the other side (don't forget that windows firewall typical blocks pings -- duh!)
Advanced Test: MTU settings you can use
If you add the mtu-test in VPN > OpenVPN > Servers > Edit > Advanced Configuration > Custom options you'll get this in the logs (don't forget to re-set it):Apr 18 23:45:40 fire openvpn[77396]: NOTE: Beginning empirical MTU test -- results should be available in 3 to 4 minutes. Apr 18 23:48:50 fire openvpn[77396]: NOTE: Empirical MTU test completed [Tried,Actual] local->remote=[1556,1556] remote->local=[1556,1556]
| I | Attachment | Action | Size | Date | Who | Comment |
|---|---|---|---|---|---|---|
| |
abea14a4bbe69dddd77cdcbda7a34dfc.png | manage | 109 K | 02 Aug 2019 - 09:52 | Main.NickDemou | Auto-attached by ImagePlugin |
| |
pfsense-openVPN-setup.png | manage | 424 K | 26 Apr 2017 - 12:43 | Main.NickDemou |
Copyright © enLogic

