Windows: quickly check if all ports of your servers are open
Installation & Configuration
- Create a folder c:\it\bin and download ps-helpers.ps1 in it:
$fname="ps-helpers.ps1"; mkdir C:\it\bin -force > $null; iwr -useb https://wiki.enlogic.gr/pub/KnowledgeBase/PublicFiles/$fname -OutFile c:\it\bin\$fname
- Create a script like this (change the host and OpenPorts):
. c:\it\bin\ps-helpers.ps1
Test-NetConnectivityToHost -RespondsToPing:$true -Host AC -OpenPorts 2382,3389,5896,10050,22001,22004,22099,47546
Test-NetConnectivityToHost -RespondsToPing:$true -Host AUDIT2 -OpenPorts 80,443,1433,3389,10050,47546
# ...
Use
Just run the script. Example output: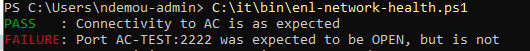
- All good at first host
- One port not open on 2nd host
Linux Tool to explore a network and find open ports
Say you have to cut the power to a company full of servers and devices and wonder if everything will be back up after restoring power. Work like this:- Save this bash file e.g. to
/opt/bin/status-network - Power off all non-important devices (e.g. workstations) and then use
fping -gornmap -snto get a list of IPs that respond to pings. These should be servers, printers, access points, etc. Their IPs are expected to stay the same (that's usually true but exceptions exist -- e.g. DHCP printers). - Create a reference file with these commands :
IPS_TO_SCAN="10.2.2.1 10.2.2.2 10.2.2.3 " #
PORTS_TO_SCAN="22,80,443,3389" #
nmap -T3 --disable-arp-ping -Pn --open -oG - -p $PORTS_TO_SCAN $IPS_TO_SCAN \
| grep Ports | sed -e 's| State:.*||' -e 's|/open[^ ]*||g' -e 's| ([^)]*)||' | sort \
> /var/log/net-status-REFERENCE.txt - Run the script and it should display an all good report (no red lines)
- From now on every time you run this script it will print in RED any changes in pings that respond and ports that are open compared to the reference report. E.g. if a server/device stops responding to pings you'll see it. If a service that uses a TCP port stops working you'll also see it.
Notes
*: Maybe do a ping sweep to find alive hosts:fping -r 2 -B 2.0 -t 25 -g 192.168.0.1 192.168.1.255 2>/dev/null | grep alive | tee /tmp/aliveAlso maybe use the aggressive scan of nmap to find more abou the hosts:
# and maybe remove some IPs based on this:
cat /tmp/alive | sed -e 's/ .*//' | xargs -i nbtscan "{}" 2>/dev/null | grep '[0-9a-f][0-9a-f]:[0-9a-f][0-9a-f]:[0-9a-f][0-9a-f]:'
IPS_TO_SCAN=`cat /tmp/alive | sed -e 's/ .*//'`
sudo nmap -A -T4 IP.ad.DR.es| I | Attachment | Action | Size | Date | Who | Comment |
|---|---|---|---|---|---|---|
| |
18cfd30e4847333a83da16620bb71867.png | manage | 6 K | 20 Jan 2026 - 15:24 | Main.NickDemou | Auto-attached by <nop>ImagePlugin |
| |
3b52d03c73b7ba1b10c6deedbadae8f5.png | manage | 24 K | 03 Sep 2023 - 19:14 | Main.NickDemou | Auto-attached by ImagePlugin |
| |
980342596dcb8c771f8ba32265525578.png | manage | 21 K | 04 Sep 2023 - 06:58 | Main.NickDemou | Auto-attached by ImagePlugin |
| |
bc00c41f63e6205b82bcc5855a56ea38.png | manage | 89 K | 13 Jun 2022 - 10:02 | Main.NickDemou | Auto-attached by ImagePlugin |
| |
fd5f04cc02225303dfdc87e3d954df49.png | manage | 98 K | 03 Sep 2023 - 12:40 | Main.NickDemou | Auto-attached by ImagePlugin |
Copyright © enLogic

